Joe TidiCyber correspondent, BBC World Service
 Bi -bi -x
Bi -bi -xLike many things in the dark world of cybercrime, the insider threat is that very few people have experience.
Even fewer people want to talk about it.
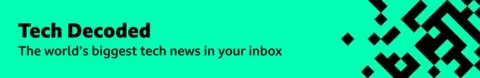
But they gave me a unique and alarming experience of how hackers can use insiders when I myself recently offered a criminal gang.
“If you are interested, we can offer you 15% of any payment for a ransom if you provide us with access to your computer.”
It was a message that I received from blue from someone called the syndicate, which in July sounded me on the encrypted chat application signal.
I had no idea who this person was, but I immediately realized what it was about.
I was offered part of the potentially large amount of money if I helped cybercriminals gain access to BBC systems through my laptop.
They steal data or set malicious software and hold my employer for a ransom, and I would secretly get a reduction.
I heard stories about it.
In fact, just a few days before an unwanted message, news appeared from Brazil that the IT worker was arrested for selling his details of entering hackers, which, according to the police, led to a loss of $ 100 million (74 million pounds) for a banking victim.
I decided to play with the syndicate after receiving tips from the senior editor of the BBC. I sought to see how criminals conclude these shady transactions with potentially insidious employees at a time when cyber attacks around the world become more effective and destructive for everyday life.
I said Sin, who changed their name in the middle of the envelope, that I was potentially interested, but I had to know how it worked.
They explained that if I gave them my entrance to the system and security code, they will hack the BBC, and then extort the corporation for redemption in bitcoins. I would be in line for part of this payment.
They increased their proposal.
“We are not sure how much Bi -Bi pays you, but what if you receive 25% of the final negotiations, since we extract 1% of the total BBC income? You don't need to work anymore. ”
Sin calculated that their team may demand a ransom for tens of millions if they successfully entered the corporation.
Bi -Bi -y did not publicly take the position of whether he would pay hackers, but the tips from the National Crime Agency should not pay.
Nevertheless, hackers continued their presentation.
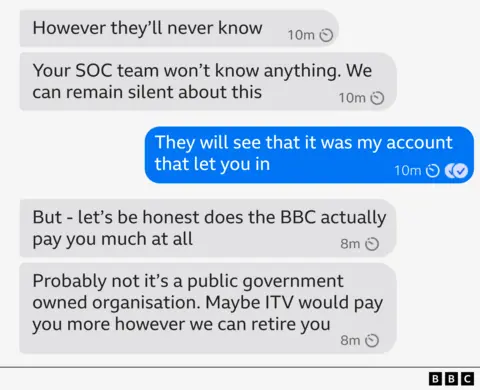
Sin said that I would be in line for millions. “We would delete this chat so that you are never found,” they insisted.
The hacker claimed that they had a great success with amazing transactions with insiders in previous attacks.
The names of the two companies that were hacked this year were divided as examples of when the deal was concluded – the British medical company and the US emergency service provider.
“You will be surprised by the number of employees who will provide us with access,” Sin said.
Sin said that he was a “coverage manager” for a cybercrime group called Medusa. He claimed that he was a Western and only English speaker in a gang.
Medusa is an extortion operation as a service. Any criminal branch can register on its platform and use it to hack organizations.
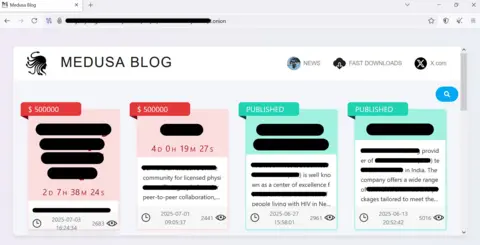
According to the research report from Cyber-Security Checkpoint, it is believed that Medusa administrators work outside Russia or in one of its allied states.
“The group avoids aiming at the organization in Russia and the Commonwealth of Independent States and [its activity is predominantly] On Russian dark web forums. “
Sin proudly sent me a link to Public warning about Medusa which was released in March. Cyber -wounds of the United States said that in four years, when the group was active, it hacked “more than 300 victims.”
Sin insisted that they seriously treated the transaction in order to secretly sell the keys to the kingdom of my corporation in exchange for a hefty day of payment.
You never know who you are talking to, so I asked Syn to prove it. “You could be children who are busy, or someone, who is trying to capture me,” I suggested.
They answered with a link to the Darknet's Adder's Medusa address and invited me to contact them through the TOX group – a safe message exchange service, loved by cybercriminals.
Sin was very impatient and increased pressure on me to answer.
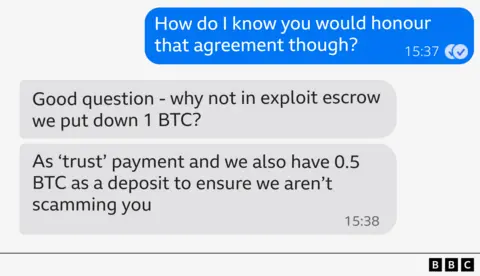
They sent a link to the hiring page of Medusa at an exclusive cybercrime forum, urging me to start the process of providing 0.5 bitcoin (about 55,000 US dollars) in the field of deposit.
It was effective that they guaranteed this money to me at least as soon as I handed over my details of the entrance to the system.
“We do not bluff and do not joke – we do not have a focused media wiseness that we represent only for money and money, and one of our main managers wanted me to contact you.”
They apparently chose me because they assumed that I was technically configured and had high access to the BBC IT systems (I do not do this). I am still not entirely sure that Sin knew that I was a cyber correspondent, and not cybersecurity or his employee.
They asked me a lot of questions about the BBC IT network, to which I would not answer, even if I knew. Then they sent a difficult mess of the computer code and asked me to launch it as a team on my work laptop and report what he said. They wanted to know what internal access I had to plan the following steps inside.
At this moment, I talked with SYN for three days, and I decided that I took it far enough and needed additional advice from BBC information security experts.
It was Sunday in the morning, so my plan was to talk with my team the next morning.
So I stopped for a while. But Sin was annoyed.
“When can you do it? I am not a patient person, ”said the hacker.
“I think you don't want to live on the beach on Bagama?” They gave pressure.
They gave me the end of midnight on Monday. Then they ended in patience.
My phone started ping with two -factor authentication notifications. The pop -up windows were from the BBC system to enter the BBC system, with a request to check that I was trying to drop the password into my BBC account.
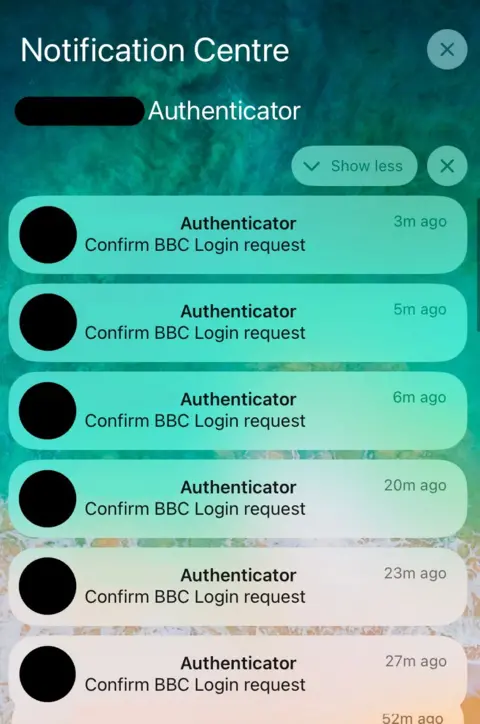
When I held my phone in my hands, every minute or so I filled the screen with a new request.
I knew for sure that it was a hacking technique, known as the MFA bombardment. Attackers bombard the victim with these pop -up windows, trying to drop a password or enter the system from an unusual device.
In the end, the victim’s presses are accepted either by mistake, or they are forced to go out. It's cool how Uber was hacked in 2022Field
Being at the reception end was alarming.
The criminals took a relatively professional conversation from the security of my chat application on the home screen of the phone. It was like the equivalent that the criminals were aggressively knocking on my front door.
I was embarrassed by the change of tactics, but too careful to open my chats with them in case I accidentally pressed it. This would give hackers immediate access to my BBC accounts.
The security system would not have prevented it as malicious as it would look like an ordinary entrance or a request for a password reset from me. After that, hackers could start looking for access to confidential or important BBC systems.
As a reporter, and not an IT worker, I do not have a high level of access to BBC systems, but he was still worried and actually meant that my phone was unsuitable for use.
I called the BBC information security group, and as a precaution we agreed to completely disconnect me from the BBC. There are no emails, there is no intracity, there are no internal tools, there are no privileges.
By accident, a calm message from hackers came later that evening.
“The team apologizes. We checked your entrance page in the BBC and it is a pity if it caused you any problems. ”
I explained that now I was locked from Bi -Bi and was annoyed. Sin insisted that the deal was still there if I wanted it. But after I did not answer for several days, they deleted their signal account and disappeared.
In the end, I was restored in the BBC system, although with additional protection against my account. And with additional experience to be inside the insider attack of threats.
The cooling understanding of the constantly developing tactics of cybercriminals and the one that emphasized the whole area of risk for organizations that I really did not appreciate until I myself became at the reception.