NEWNow you can listen to Fox News articles!
Cybercriminals continue to find new ways to aim at users of social networks, and Meta remain one of the most common baits. Loss of access to Facebook or Instagram can have real consequences for both individuals and business, which makes people more likely to fall in love with urgent security warnings. Attackers use this, sending convincing notifications that give you quick actions without hesitation.
This is exactly what does New Filefix campaign So dangerous; It looks like ordinary accounting, but this is really a trap.
Subscribe to my free Cyberguy report
Get my best technical councils, urgent security notifications and exclusive offers, concluded directly in your mailbox. In addition, you will get instant access to my final guidance for survival of fraud – for free when you join my Cyberguy.com/newsletter
How fake Microsoft warnings are deceiving you in phishing fraud
Cybercriminals are aimed at Facebook and Instagram accounts, sending fake security warnings. (Fox News)
How the Filefix attack works
As reported Researchers in acronis, The leading company for the protection of cybersecurity and data protection, the attack begins with a phishing page that looks like a message from the META support group, claiming that your account will be disconnected within seven days if you do not see the incident report. Instead of providing an actual document, the page masks the malicious PowerShell command as a file path.
The victims give an instruction to copy it, open File Explorer and insert it into the address line. Although it seems harmless, this action secretly launches the code that launches the process of infection of malicious programs.
This method is part of a family of attacks, known as Clickfix, where people are deceived into the team inserts into system dialogs. Filefix, created by the RED Team Mr.D0X researcher, relies on this idea, using the address line of the file researcher instead. In this campaign, the attackers improved the trick, hiding the malicious command behind the long lines of the spaces, so only a fake file is visible for the victim.
The hidden script then loads what looks like a JPG image from Bitbucket, but the file contains a built -in code. After execution, he extracts another scenario and deciphers the final useful load, bypassing many safety tools in the process.
Do not fall in love with this banking trick for Phishing fraud
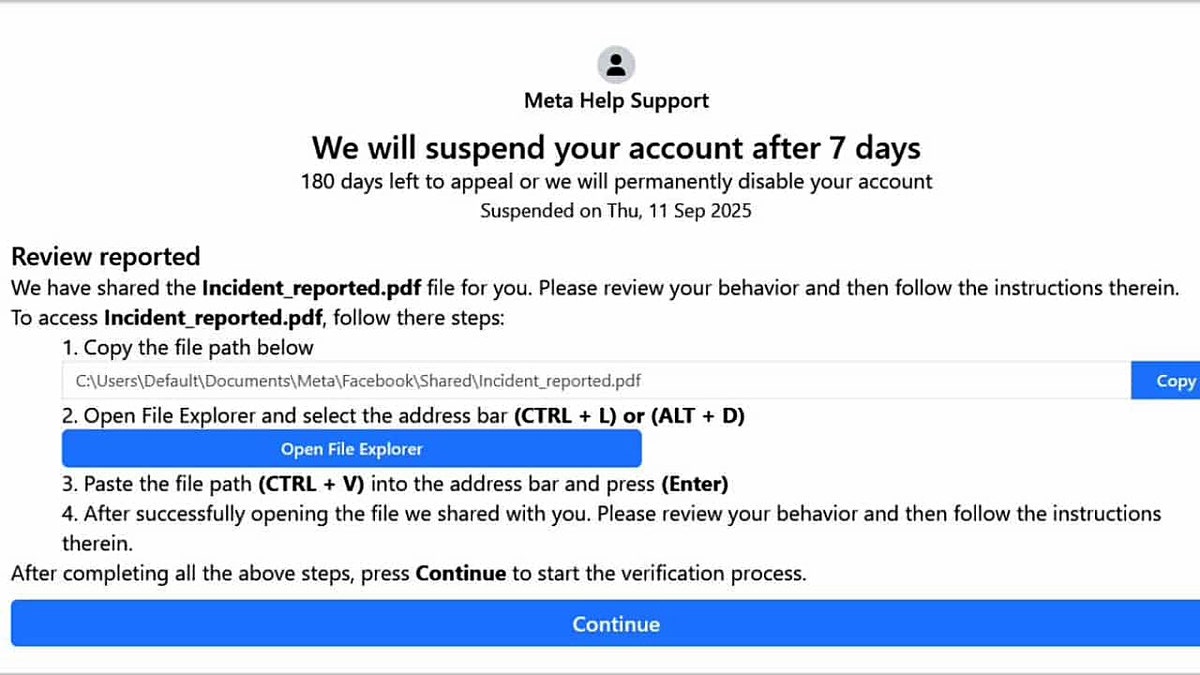
Filefix sends false alerts that call users to view the safety of their account. (Acronis)
That theft is trying to steal
The adoption provided by this campaign is STERC, an infants, which collects a wide range of personal and organizational data. It is designed to obtain accounting data browser and authentication cookies from Chrome, Firefox, Opera and other browsers.
It is also aimed at reporting applications such as Discord, Telegram and Pidgin, as well as cryptocurrency wallets such as Bitcoin, Ethereum and Exodus. Stearc goes further, trying to jeopardize cloud accounts from Amazon Web Services (AWS) and Azure, VPN services, such as ProtonVPN and even game accounts from Battle.net and Ubisoft. In addition, he can take the screenshots of the desktop of the victim, giving attackers a living idea of sensitive activity.
Acronis said that the campaign has already appeared in several different versions in a short time, with changes in useful loads and infrastructure. This suggests that attackers are actively testing and improving their methods to avoid detecting and improving success indicators.
Meta deleys 10 million accounts on Facebook this year, but why?
Stearc is also aimed at VPN software and cryptocurrency wallets. (Istock)
5 ways to protect yourself from Filefix attacks
To remain protected from attacks, such as Filefix, and prevent harmful software, for example, steal confidential information, you need to combine caution with practical security measures. The following steps can help in protecting accounts, devices and personal data.
1) Skeptical of urgent warnings
Attackers rely on panic. Treat any message that claims that your throwing account or other services will be disabled within a few days with caution. Check the alert directly through the official platforms, and not press links or the following instructions from e -mail or web page.
2) Avoid copying commands from unknown sources
Filefix is supposed to convince you to insert the hidden PowerShell commands, disguised as file paths. Never insert commands into system dialogs, files or terminals if you are absolutely sure of their origin.
3) invest in personal data deletion services
Filefix and theft flourish in the information that they can extract from the device or related accounts. Using data deletion services, you reduce the amount of confidential personal information that can be found on the Internet or left on old platforms. This minimizes that attackers can use if they manage to access.
Despite the fact that no service can guarantee the complete removal of your data from the Internet, the data removal service is really a reasonable choice. They are not cheap, like your confidentiality. These services do all the work for you, actively monitoring and systematically wash your personal information from hundreds of websites. This is what gives me peace of mind and turned out to be the most effective way to erase your personal data from the Internet. By limiting the available information, you reduce the risk of cross -country cross -fraudsters from violations using the information that they can find in a dark web, which complicates their aiming.
Check out my best elections for data deleting services and get a free scan to find out if your personal information is already displayed on the Internet by visiting Cyberguy.com/delete
Get a free scan to find out if your personal information is already on the Internet: Cyberguy.com/freescan
4) install reliable antivirus software
Strong antivirus software can detect malicious software, for example, Starec before it is completely performed. Many decisions currently include a detection on the basis of behavior that can mark suspicious scenarios or hidden loads, helping to catch threats, even when attackers are trying to disguise the teams as harmless actions.
The best way to protect yourself from malicious links that set malicious software, potentially access to your personal information, is to establish strong antivirus software on all your devices. This defense can also warn you about e -mail and extortion fraudsters, preserving your personal information and safety assets.
Get your elections for the best winners of the 2025 antivirus protection for your devices Windows, Mac, Android & iOS Cyberguy.com/lockupyourtech
5) Use password manager
While Filefix is aimed at saved accounting data, using an authoritative password dispatcher reduces risk, creating unique passwords for each site. Thus, even if one browser or application is compromised, attackers cannot access your accounts in other places.
Next, look if your email was disclosed in past violations. Our password manager (see Cyberguy.com/passwords) includes a built -in violation scanner that checks whether your email or password address has appeared in known leaks. If you find a coincidence, immediately change any repeated passwords and fix these accounts with new, unique accounting data.
Check the best reviewed password managers in 2025 in Cyberguy.com/passwords
Click here to get the Fox News application
Kurt key removal
Cybercriminals continue to find creative ways to deceive users of social networks, and Filefix proves how convincing these frauds may look. A fake meta -ownership can feel urgently, but to pause before pressing or copying something, the best protection. Relying on strong habits and safety tools gives you an advantage. Data deletion services, antivirus software and password managers on the RASE Risk reduce risk. When you unite them, you become much more difficult for the attackers to turn the tactics of fright into a real threat.
Should platforms such as META make more to warn users about this developing phishing tactics? Let us know by writing to us in Cyberguy.com/contact
Subscribe to my free Cyberguy report
Get my best technical councils, urgent security notifications and exclusive offers, concluded directly in your mailbox. In addition, you will get instant access to my final guidance for survival of fraud – for free when you join my Cyberguy.com/newsletter
Copyright 2025 Cyberguy.com. All rights are protected.








